Cryptography Collection
Cryptography, the art of secret communication, has a rich history intertwined with brilliant minds and groundbreaking inventions
For sale as Licensed Images
Choose your image, Select your licence and Download the media
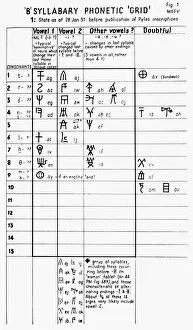
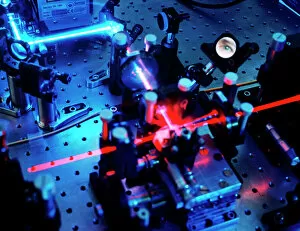
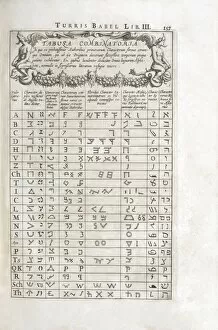
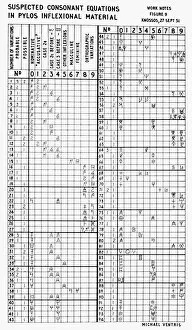
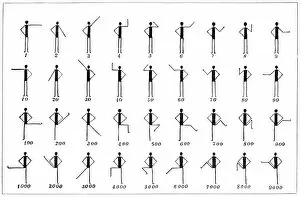
Cryptography, the art of secret communication, has a rich history intertwined with brilliant minds and groundbreaking inventions. One such luminary is Alan Turing, the British mathematician whose pioneering work in cryptography during World War II helped crack the infamous Enigma code used by the Germans. His contributions laid the foundation for modern cryptography. In 1951, cryptographer Michael Ventris achieved a remarkable feat by deciphering the Minoan Linear B script using his first grid. This breakthrough shed light on an ancient civilization's language and opened new doors for linguistic exploration. Fast forward to today, where quantum cryptography equipment stands at the forefront of data security. With its ability to harness quantum mechanics principles, this technology ensures unbreakable encryption that even powerful computers cannot unravel. Speaking of which, quantum computer cores are revolutionizing computing capabilities as they possess immense processing power far beyond traditional machines. However, let us not forget historic artifacts like the Military Enigma I Machine from 1941 or Charles Babbage's innovative designs depicted in caricature C015 / 6701. These objects remind us of our cryptographic roots and how far we have come since then. Throughout centuries, great minds like John Wallis in 1825 or linguistics tables from the 17th century have contributed their expertise to advance this field further. Their dedication paved the way for future generations to explore new frontiers in securing information. Conceptual artwork C016 /7539 symbolizes data security—a vital aspect protected through cryptographic techniques—ensuring confidentiality and integrity across various domains. As we delve into cutting-edge technologies like quantum computing (depicted in C013 /6173), it becomes clear that cryptography remains indispensable in safeguarding sensitive information against malicious actors seeking unauthorized access. Finally, let us acknowledge SIGABA—the cipher machine developed during World War II—which played a crucial role in encrypting and decrypting secret messages for American government agencies until well into the mid-20th century.